Emerging Threats: Violent Online Groups and AI-driven Exploitation
**Trigger Warnings: CSA/exploitation, blackmail, violence, crimes against children, SVU**
Panelists:
Chris Hansen (from Takedown with Chris Hansen, To Catch a Predator), Greg Shiller (CEO, Child Rescue Coalition), Michelle DeLune (President and CEO at National Center for Missing and Exploited Children), Ash Thorne (Supervisory Special Agent with the FBI’s Denver Field Office)
Chris Hansen hosted the devastating panel about how the most innocuous images can begin a swell of trauma for families through the use of scraping publicly available photos, chat apps, and gaming systems. Hansen became famous for hosting the show, To Catch a Predator, where he and a team of law enforcement would make contact with predators online as fictional children. He started his own network, TruBlu (watchtrublu.com), on which he hosts his current show, Takedown with Chris Hansen. His decades of experience catching adults who target vulnerable children and families online make him a qualified person to host this CrimeCon panel about disturbing crimes.
“Every predator has never had just one victim.”—Greg Shiller
While the panel discussion was gut-wrenching and heartbreaking to sit through, this stalwart group of four people intended the time to show more than what the risks are of being online. They did what they could to convince the audience that help for families and individuals is out there. NCMEC wants children to know they are not alone if they fall into the trap of predators. It is unfortunately, common. We saw this in real time. NCMEC has a site for reporting and will do everything possible to get exploitative images taken down whether the images are genuine, altered, or made from AI. report.cybertip.org
The National Center for Missing & Exploited Children is a private, non-profit 501(c)(3) corporation whose mission is to help find missing children, reduce child sexual exploitation, and prevent child victimization. NCMEC works with families, victims, private industry, law enforcement, and the public to assist with preventing child abductions, recovering missing children, and providing services to deter and combat child sexual exploitation.
Some funding for the massive operations of NCMEC come from the US Dept. of Justice, but it is not a government agency. This is a non-profit with 501(c)(3) designation and needs donations. This organization runs the AMBER alert system, something you may know about if you’ve never heard of NCMEC. The NCMEC.org website is filled with so much information about what crimes are, what predators do, downloadable tip sheets, age-appropriate slideshows, and a lot of explanations allowing people with no experience to read up on the dangers children face online and in person.
Today’s Impacts
Predators are leveraging AI to get recruits. This begins with the process of grooming, a word that is frequently misused by bigots these days because they panic when a transwoman wants to lead storytime at a library. Specifically going after children online follows the same formula, but the actions are carried out differently. Once someone is victimized, they may be offered relief (a way to not be the target anymore) if they’re willing to be a recruit for the C.Sex Trafficking network.
- In 2023, the CyberTipline received more than 186,800 reports of online enticement.
- Between 2021 and 2023, the number of online enticement reports increased by more than 300%.
- In 2024, through October 5, NCMEC received more than 456,000 reports of online enticement.
The explicit photos are used for dominance and power, according to Michelle DeLune. She said they are not obtained for sexual gratification; they are sold/passed on to people who seek that. There’s a supply and demand economy. She warned that a child could believe they’re chatting with only one person, when in reality, that other username/ID is shared by a whole group of predators.
SSA Thorne vaguely described some of the horrendous ways these criminal groups abuse their targets. They make the children violate themselves or another child in the house; they’ll demand self-harm behaviors; they’ll demand animal abuse—all under that threat to do what they’re told or what’s being done will be shown to everyone the child knows. Thorne tried to emphasize how staggeringly large these networks and criminal empires are and that they are usually not built on one type of crime. If children are being kidnapped and trafficked, there’s another branch handling the cyber abuses, another that could be moving drugs, weapons, or any number of other illegal activities.
Offenders are producing their own material by taking a child’s face from a social media photo and using AI to create the content they want to market. Law enforcement, at first glance, doesn’t even know if a photo that comes to their agency is real. He said the “764” empire is one of the most wildly spread criminal groups which frequently changes name. Greg Shiller said, “Nothing has scared me as much as 764 as a prosecutor.” He added, “Every predator has never had just one victim.”
- Predators typically have between 50 and 150 victims over the course of their lifetimes.—childrescuecoalition.org
DeLune explained about modern software apps that are easy to get and use. The term is “nudify” apps—a photo is uploaded, a button is pushed, and the software removes the clothing of the person in the photo. It’s not their real body, but nonetheless, degrading, humiliating, and harmful.
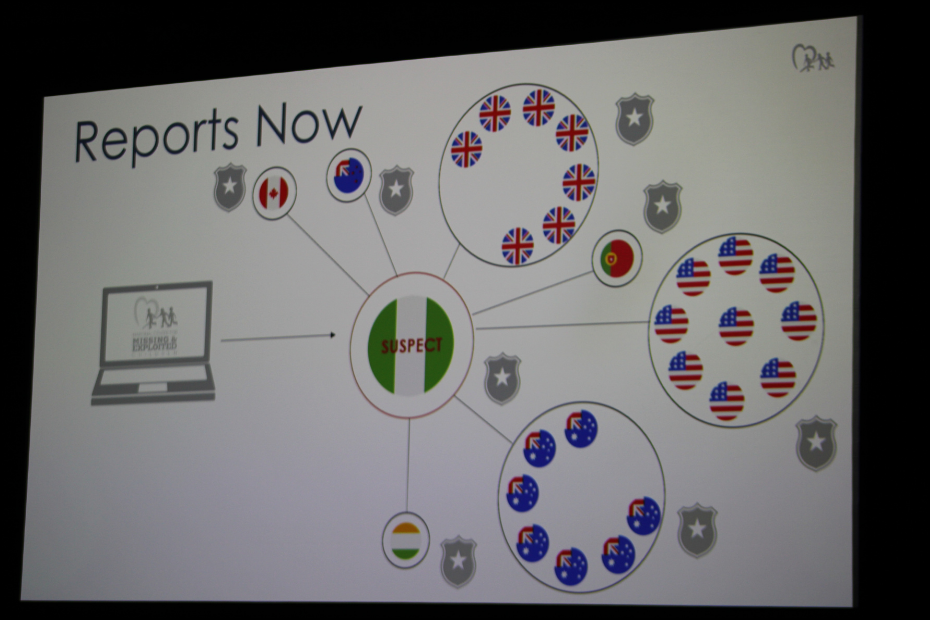
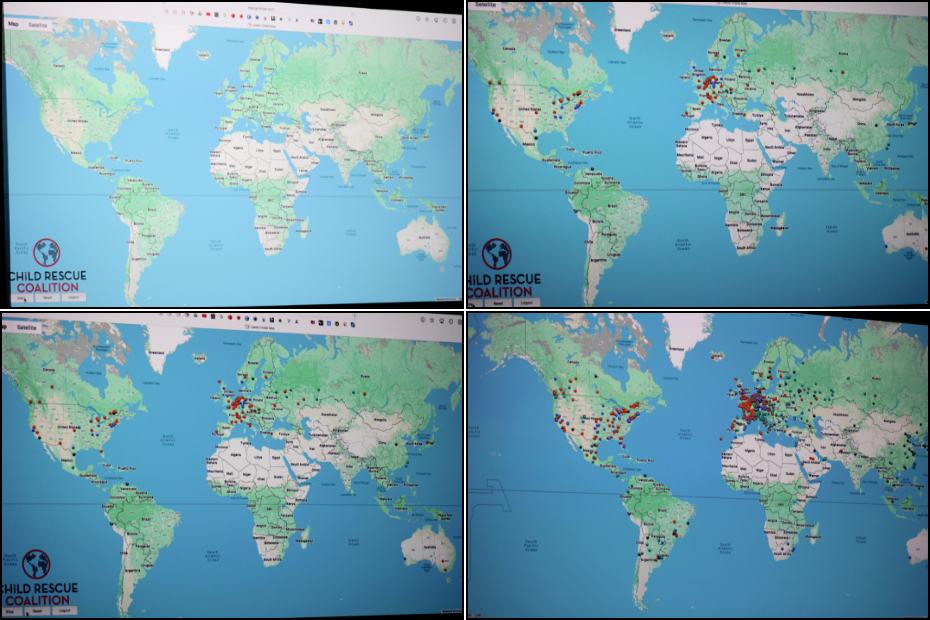
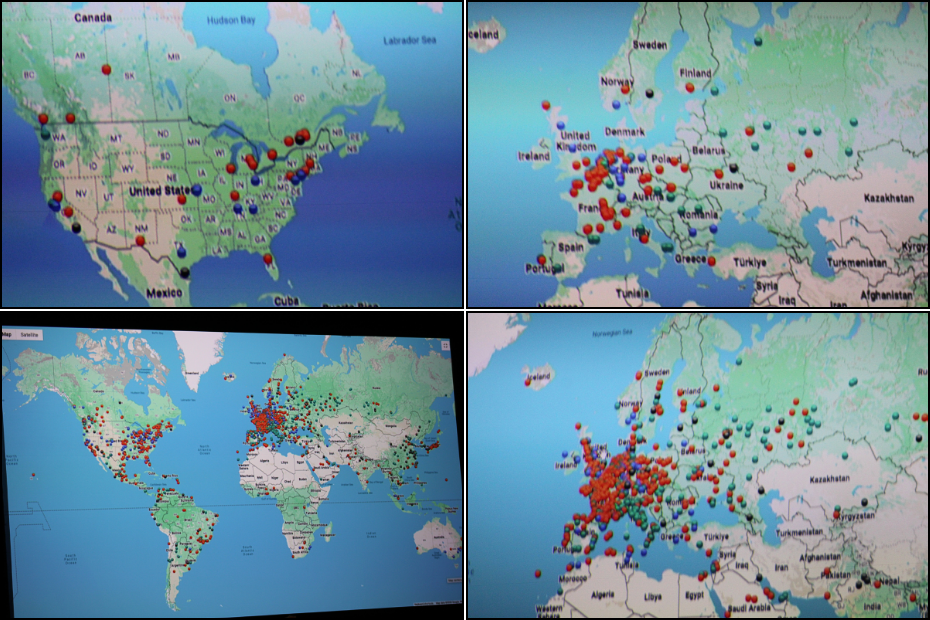
Child Rescue Coalition has new technology to track CSA, exploitation and extortion predators in real time. Any law enforcement agency—no matter how small—can request their training & access. Greg Shiller booted the software to show the audience its power. The global map begins with the shapes, colors, and names you’d see on a classroom geography map. After mere seconds, dots of different colors pop up on the map like measles. These hot spots of activity on the networks change as those time zones move from typical working hours to sleeping hours. The different colors reflect the different networks.
If you watch police dramas like Criminal Minds or Law & Order: SVU, you would have seen unreasonably fast response times of ethical hackers working for law enforcement. They throw around jargon like: IP address, VPNs, geolocation, MAC address, ransomware, etc. The shows are pretty accurate to my own understanding of how the new Child Rescue Coalition real time software works. It’s brilliance + innovation + compassion. It’s a way to identify these criminals, even if most can’t be prosecuted. Their networks can get shutdown as a starting place.
Effects of Trauma and Shame
According to the panelists and coming specifically from Michelle DeLune, children are actively trying to exploit other children. The why, the motivation, may be different or the same as why an adult would do it. SSA Thorne said that a child faces punishment for not complying which could be threats, doxxing, SWATting, uploading/sending content to people (family) of the victim.
To paraphrase DeLune: These kids need to know they will not be punished for coming forward. They need to know to go to NCMEC and law enforcement and also, DO NOT PAY the people demanding money and compliance.
Everyone on this panel agreed that the tech industry bears responsibility. DeLune said, “Some companies are doing good things, but not overall.” There were no safeguards at the beginning of the internet and the beginning of social media. Now there are some. VPNs can lead to dead ends, unfortunately. History is repeating itself with AI. No protections. No laws or regulations.
Outcomes
Parental controls won’t work unless you talk to your kids. “We have to talk to our kids. Normalize even embarrassing conversations,” SSA Thorne said. Parenting is hard. Kids are more likely to listen to a peer. This is where NCMEC’s library of resources can help by educating people on the red flags and where to report the solicitation or abuse.
Synthetic content does not have the same punitive damages even though it encourages more of the same.
One audience member wanted to know if there was new data showing women are more predatory than previously believed. The answer wasn’t cut and dry. Michelle DeLune said female predators are more likely to know their victims. Hansen reflected on how the teacher/student boundary used to be played off as every teen boy’s dream. As for the numbers, Greg Shiller had some: of his 250 convictions, 5 were women; of those, 4 of them knew their victims.
Links
- NCMEC main site
- Child Rescue Coalition